On December 14, 2021, the Lodestone Forensic Investigations team responded to a client whose environment was affected by what appeared to be a new strain of ransomware: White Rabbit. Lodestone identified via open-source intelligence (OSINT) that White Rabbit was first publicly disclosed on Twitter on the same date by security researcher Michael Gillespie (@demonslay355).
Based on tactics, techniques, and procedures (TTPs) observed in ongoing investigations and further research, Lodestone has determined that the White Rabbit group may be affiliated with known threat actor group FIN8. FIN8 is a financially motivated group active since 2016 that has targeted retail, restaurant, and financial institutions using social engineering and spear-phishing attacks. Additionally, FIN8 has been linked to backdoor malware PUNCHBUGGY and BADHATCH, and the memory scraping malware PUNCHTRACK. The White Rabbit ransomware group appears to have leveraged a previously unseen version of BADHATCH which, based on characteristics of the malware sample acquired, Lodestone has named F5.
Lodestone has made preliminary observations of White Rabbit behavior that are described in the text and screen captures below.
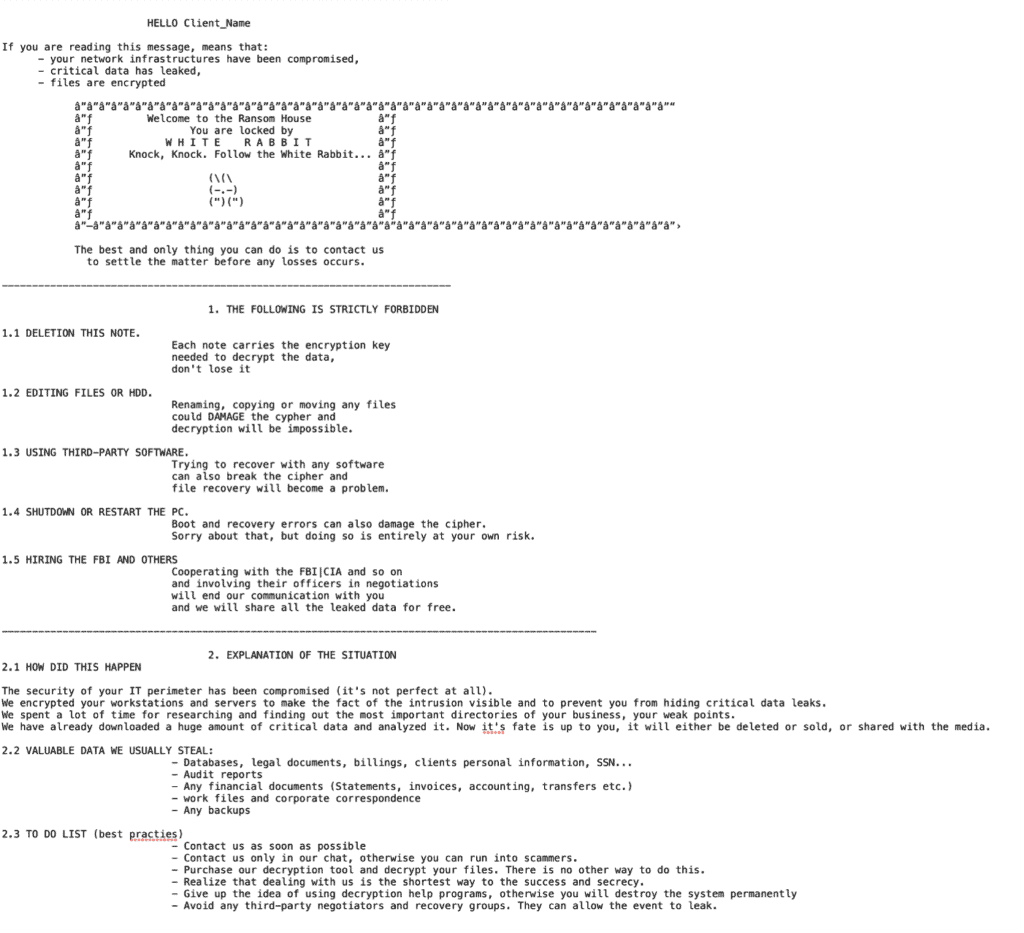
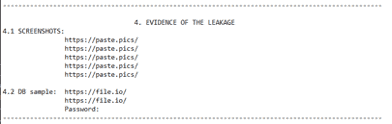
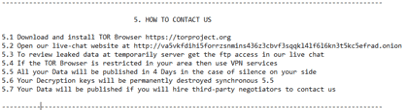
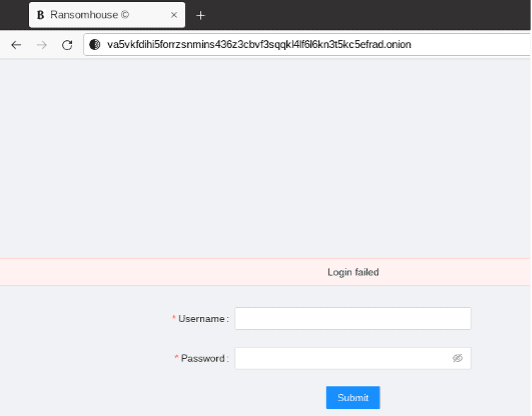
At the time of writing, the earliest evidence of compromise Lodestone has observed in its investigations was a PowerShell script that executed on July 10, 2021. An analysis of PowerShell script artifacts revealed script blocks that matched those described in a July 27, 2021, Bitdefender article on FIN8. Additional White Rabbit activity Lodestone observed occurred on December 11, 2021; while the PowerShell artifacts from this most recent event were similar to those associated with activity from August 30, 2021, these were not an exact match.
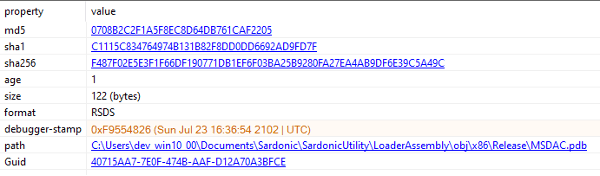
Lodestone’s analysis of a White Rabbit sample from August 30, 2021, suggested that it was an updated version of FIN8’s BADHATCH malware, also known as SARDONIC, that contains the following PDB path:
“C:\Users\dev_win10_00\ Documents\Sardonic\SardonicUtility\LoaderAssembly\obj\x86\Release\MSDAC.pdb”.
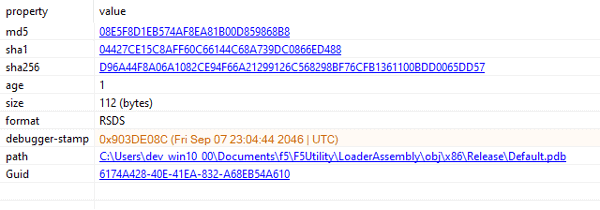
The December 11, 2021, sample, however, contains the PDB path below:
“C:\Users\dev_win10_00\Documents\f5\F5Utility\LoaderAssembly\obj\x86\Release\Default.pdb”.
The exact relationship between the White Rabbit group and FIN8 is currently unknown. However, Lodestone identified a number of TTPs suggesting that White Rabbit, if operating independently of FIN8, has a close relationship with the more established threat group or is mimicking them.
Lodestone will continue to provide updates with additional findings on this emerging threat.
Indicators of Compromise
IP Addresses
- 170.130.55[.]120
- 104.168.132[.]128
Domains
- 104-168.132[.]128.nip[.]io
URLs
- https://104-168-132-128.nip[.]io /51b16c
- http://va5vkfdihi5forrzsnmins436z3cbvf3sqqkl4lf6l6kn3t5kc5efrad[.]onion
Filenames
- “default.dll”
Hash Values
- 655c3c304a2fe76d178f7878d6748439 (“default.dll”)
- 6ffa106ac8d923ca32bc6162374f488b (Sardonic PowerShell script)
- fb3de0512d1ee5f615edee5ef3206a95 (Sardonic x86 DLL)
- 4a03238e31e3e90b38870ffc0a3ceb3b (Sardonic x64 DLL)
- Beffdd959b1f7e11e1c2b31af2804a07 (F5 PowerShell script)
- d9f5a846726f11ae2f785f55842c630f (F5 x86 DLL)
- 087f82581b65e3d4af6f74c8400be00e (F5 x64 DLL)
Additional Information and References
- Michael Gillespie’s White Rabbit announcement on Twitter:
🔒 #Ransomware Hunt: "White Rabbit" with extension ".scrypt", drops note for each encrypted file with "<filename>.scrypt.txt" with victim-specific information: https://t.co/ZjVay8A3Ch
— Michael Gillespie (@demonslay335) December 14, 2021
"Follow the White Rabbit…" 🐰🤔 pic.twitter.com/lhzHi5t1KK
- Bitdefender on FIN8:
- MITRE profile on FIN8
- PUNCHBUGGY and PUNCHTRACK


